Top 10 Best Secure Coding Practices
Penetration Testing
5 MIN READ
January 5, 2021
![]()

As cyberattacks increase, security is a key feature that a coder has to ensure. Secure coding practices play a significant role in software security that encompasses databases, applications, and other digital systems. The software developers should be capable of writing code that can withstand emerging threats. So, a programmer must code responsibly and write high-quality and secure codes as much as possible.
What are secure coding practices?
Secure coding can be defined as the practice of software development that protects itself against security vulnerabilities. Coding deficiencies, bugs, and logic errors are the primary reasons behind the common vulnerabilities that are exploited. By analyzing hundreds of such reported breaches, experts have found that only a few number of software coding errors have been leveraged by the attackers in most cases.
Why Is Secure Coding Important?
Organizations may take proactive measures to substantially minimize or remove bugs in advance by detecting inappropriate coding practices that contribute to security problems and educating developers on safer alternatives.

Threat Modeling
A crucial part of safe coding is to identify the biggest threats & risks faced by the applications. You will certainly not be able to solve all problems immediately and all of the time, but you will be aware of what is needed and can easily identify the important assets & the vulnerable ones.
Keep Security Simple
Complexity is not good for security. It gets overburdened and fails. Too many mixtures of processes and tools can have repercussions. The goal should be to make the security features as simple as possible so that it can be well understood and adopted by every user.
Positive Security
Simply make provisions for what is allowed while rejecting every other thing. Also known as whitelisting, it is considered a very efficient method to prevent unwanted attacks. This limits the attack surface to the number of risks accepted through threat modeling.
Validate Input
Inputs from all the untrusted data sources must be validated. This eliminates a major chunk of software vulnerabilities. Validate the external data sources including network interfaces, command-line arguments, user-controlled lines, and environmental variations, etc.
The Principle Of Least Privilege
Each function in the coding must execute by utilizing the least number of privileges that are necessary to complete a job. A permission window must match the least time needed to execute the job. If coders adhere to this approach, it curtails the chances of attack by reducing the opportunities for an attacker to run arbitrary codes with extra privileges.
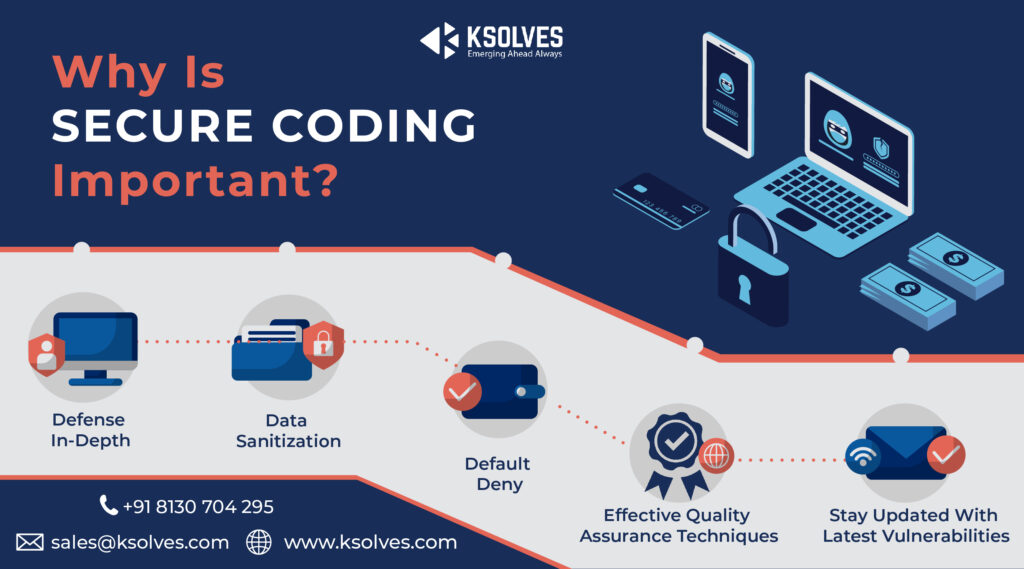
Defense In-Depth
A multi-layered defensive strategy can manage risks in a better way. Even if one layer of defense is breached, the other layer might respond to prevent the breach spiral into a vulnerability. This limits the risks of a successful exploit.
For instance, you can couple secure runtime mechanisms with secure coding practices. This reduces the possibility of a security flaw(in coding) getting exploited in runtime environments.
Data Sanitization
Every chunk of data that is being passed to sophisticated subsystems like relational databases, command shells, etc must be sanitized. By using commands, SQL, or other forms of injection attacks, attackers can invoke the unutilized functionalities to breach the system.
Default Deny
Access decisions should be based on permissions and not on exclusions. This essentially means that access will not be granted by default, and the protection mechanism will detect the conditions that allow access on a case-to-case basis.
Effective Quality Assurance Techniques.
This is something you should look for after the coding is done. To effectively detect and eliminate vulnerabilities, deploy quality assurance techniques. Penetration testing, source code audits, fuzz testings must be incorporated to create a robust quality assurance program.
Stay Updated With Latest Vulnerabilities
The security scenario is always evolving and the best practices of today might fail to withstand the threats of tomorrow. A coder must have a keen eye on the emerging threats so that the coding can anticipate future threats and eliminate them.
Closing Thoughts:
So, you are now equipped with the 10 best secure coding practices that will guide you to code in the safest way possible. A single successful attack can cause a lot of damage to businesses and organizations. Thus, keeping an eagle’s eye during the development phase is an easy way to stay on the front foot! To know more about secure coding, you can talk to our experts.
Email : sales@ksolves.com
Call : +91 8130704295
![]()




Author
Share with