Overview of Salesforce Data Security Model
Salesforce
5 MIN READ
March 24, 2021
![]()
Data security has become an integral part of organisations across the globe. To adequately provide security that meets all aspects of business, Salesforce has a flexible & robust security model that verifies data at every possible corner. This blog will enlighten you with the Salesforce data security.
Salesforce restricts the presentation of information in order to preserve confidentiality in various dimensions. Salesforce verifies users to keep a strategic gap from access to information by unauthorised users. For user validation, Salesforce utilizes an array of techniques that are appropriate for hierarchical requirements. It may include two-Factor authentication, network-based security, password, session security, and much more.
Stages of Salesforce Data Access
As your organization generates data, you can regulate the access of users to it. Whether it is a particular field, article, or an individual record, you can set up its security protocols.
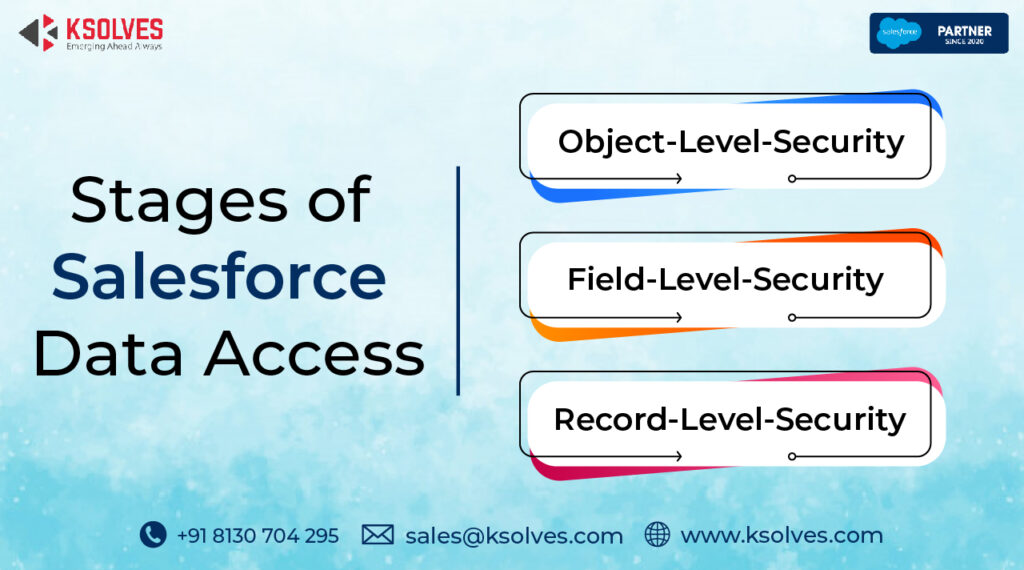
1. Objects:
The most simple thing to monitor is the access to object-level data. By introducing consents to a certain form of item, you can oversee a group of users as they access, create, modify, or delete records of the object.
For example, object authorizations can be used to confirm that interviewers can view vacant positions & employee applications but can’t change or delete them.
Functioning Of Object Level Security:
- Profile: Object-level security is defined by assigning profiles to different users. You can set up and restrict the CRED (Create, Read, Edit, Delete) permissions for every profile that is set up.
- Permission sets: These are utilized to accommodate extra permissions to users who have been assigned a profile already.
2. Fields:
You may limit access to particular fields even if a client never approaches the object. For example, it is possible to make the compensation domain hidden to the interviewers which can be shown only to the supervisors & enrolment personnel.
How can you administer Field-Level Security?
- Go to the Setup. Follow it up by clicking on Administer> Security Control. Go to Field Accessibility.
- A list of objects in the organization is displayed. Opt for the object whose field has to be altered.
- Simply opt for your view. If View by field is selected, field-level security for only one field can be accessed. If View by Profile is selected, field-level security for various fields can be accessed.
- To edit field access, choose the specific field from the drop-down menu. From field accessibility for the field, simply click on the link. Two choices are there- Visible and Read Only.
- If Visible is selected, the field becomes readable as well as editable.
- If Read Only is selected, the field becomes visible but can not be edited.
- Finally, click on the Save button.
3. Records:
You may allow specific users to view an object while restricting the individual object records from them that they are not allowed to view. For example, the interviewer can be allowed to view & modify his/her own records while restricting access to the audits of other interviewers.
You can supervise record-level access in four separate ways:
1. Organization-wide defaults
Organization-wide defaults imply the default user access dimension of each other’s data. The settings of organization-wide sharing can be utilized to protect data to the most limiting dimension. It can be followed with record-level protections & sharing tools to particularly provide access to various users.
- Organization:
At the organization level, you can create a complete list of approved users, set up the password approaches, and restrict logins to particular hours/areas.
Functioning Of Organization Level Security:
- IP Restrictions can be imposed. The IP addresses can be specified from which the users are permitted to log in.
- Utilizing Trusted IP Ranges, it is possible to restrict the user’s ability to sign in only when they are at the office or a specific place. If any attempt is made to log in from outside the range, two-factor authentication will kick in. The user needs to enter a code that will be sent to their phone.
- Login Access time can be limited. It specifies the times when the users can sign in.
- It is also possible to specify & restrict the hours for the users to log in based on their profile.
- Password Policies allows you to mention a specific timespan after which all the passwords of users expire. It is also possible to define the complexity level for the passwords. You can even customize the settings in such a way that the passwords expire for a batch of users except for a few with special permissions.
2. Role hierarchies
Role hierarchies provide access to users who are positioned higher in the chain of command. They are eligible to access the records held by users who’re placed below them in the organizational ladder.
3. Sharing Rules
Sharing rules are designed for special cases that are implemented as association-wide defaults. They are focused on particular user gatherings to allow them access to certain records that they can’t view in general. Sharing rules are only utilized to provide access to records to additional users. They are not as strict as the default association-wide protocols.
4. Manual Sharing
Manual sharing allows the owners of certain documents to share them with various users. Although it is not organized like organization-wide sharing environments, it can be beneficial in certain situations. For example, it can be utilized by an enrollment personnel who is taking an off day to allocate his records to someone else to ensure zero disruption in the workflow.
What does Salesforce standard security include?
Salesforce data security should address a wide range of potential vulnerabilities in the system. Here are some essential aspects of the Salesforce data security model–
- Access control
The basic level of data security in Salesforce is access control. Login screens need to be protected. Encourage the team to have strong passwords. These passwords need to be changed often. Two-factor authentication is always the best option.
- Self-hosting vs Cloud hosting
We know that Salesforce is hosted in the cloud. This can create several security challenges. Choosing self-hosting offers you extra protection. Self-hosting is expensive however, it allows you to access customizable data security options.
- Updated user permissions
The more people will have access to the data, the more vulnerable data will be. Overexposure is a major issue in data security. Updated user permission ensures that only authorized users can have access.
- Frequent audits and reports
Another aspect of Salesforce data security is audits and reports. Your salesforce data security model needs to check audits and reports for data breaches. You should always monitor access logs and check people who are accessing your systems. Monitor any unauthorized logs or other signs for security breaches.
- Communicate best practices to your team
Communication is a powerful tool for data security in Salesforce. Poor practices result in data breaches and loss. Give clear and concise instructions to secure your Salesforce environment from threats.
These include strong passwords, avoiding access on personal devices, locking the computer when away, and many more.
- Ensure strong code
The software releases from Salesforce offer more functionalities and security. However, this is only possible if the code is error-free. Static code analysis tool helps in verifying the validity of coding structure.
Improper functionality creates security issues. It is better to find the errors earlier and fix them.
- Current data backup
As far as Salesforce data security is concerned, no one can promise that you will never experience any data loss. Preparing yourself is always the smartest choice you can make.
A backup of your data is important to maintain the highest data security in Salesforce. Ksolves will help you with a reliable backup tool to safeguard your data.
- Data recovery
Data backup is just not enough. You must know ways to restore the backed-up data effectively. You need to configure your recovery tool as per your needs. Every business has different requirements. Ensure your data backup is addressing your needs.
- Regulatory compliance Awareness
Many organizations have sensitive data that needs to be secured at all times. Industries such as banking, insurance, etc, must be informed about government regulations.
Some regulations suggest protecting the personal information of their customers, employees, and clients. A failure to do so can result in penalties and fines.
End Note:
Ensuring data security is essential in a world where cyberthreats are posing challenges every day. Users must be able to access all the data they require but should not have access to the realms of data they are not entitled to. Salesforce recognizes this & provides several ways to shield your data as demonstrated above.
But you can’t do everything alone. You need a partner that can help you with every step. What better than Ksolves. As a leading Salesforce development company, Ksolves is known for its high-end Salesforce data integration, Salesforce migration services and customizable Salesforce apps. We have some stalwart Salesforce experts that not only guide you but also watch your back for every issue that you face in the journey of creating a Salesforce data security model. For further information, you can contact the certified Salesforce experts of Ksolves!
Email : sales@ksolves.com
Call : +91 8130704295
Read Related Articles –
Selecting Your Salesforce CPQ Consulting Partner: Top Things To Consider
Why Opt For The Salesforce CPQ Software For Your Business
![]()
AUTHOR

Salesforce
Md. Asad Khan, an expert Technical Project Manager at Ksolves, who is a certified Salesforce architect at Ksolves, brings 7+ years of experience. He specializes in FSL, B2B, Service & Sales Cloud, and Non-profit cloud, excelling in APEX, Aura Component Framework, Lightning Components, Triggers, Visualforce, and creating insightful dashboards and reports.
3 thoughts on “Overview of Salesforce Data Security Model”
Leave a Comment Cancel Reply







I could think of a dozen more. That’s how important cybersecurity is in today’s world.
The article was very informative which I have already shared with my colleagues and they loved it. Thanks again.
Thank you!